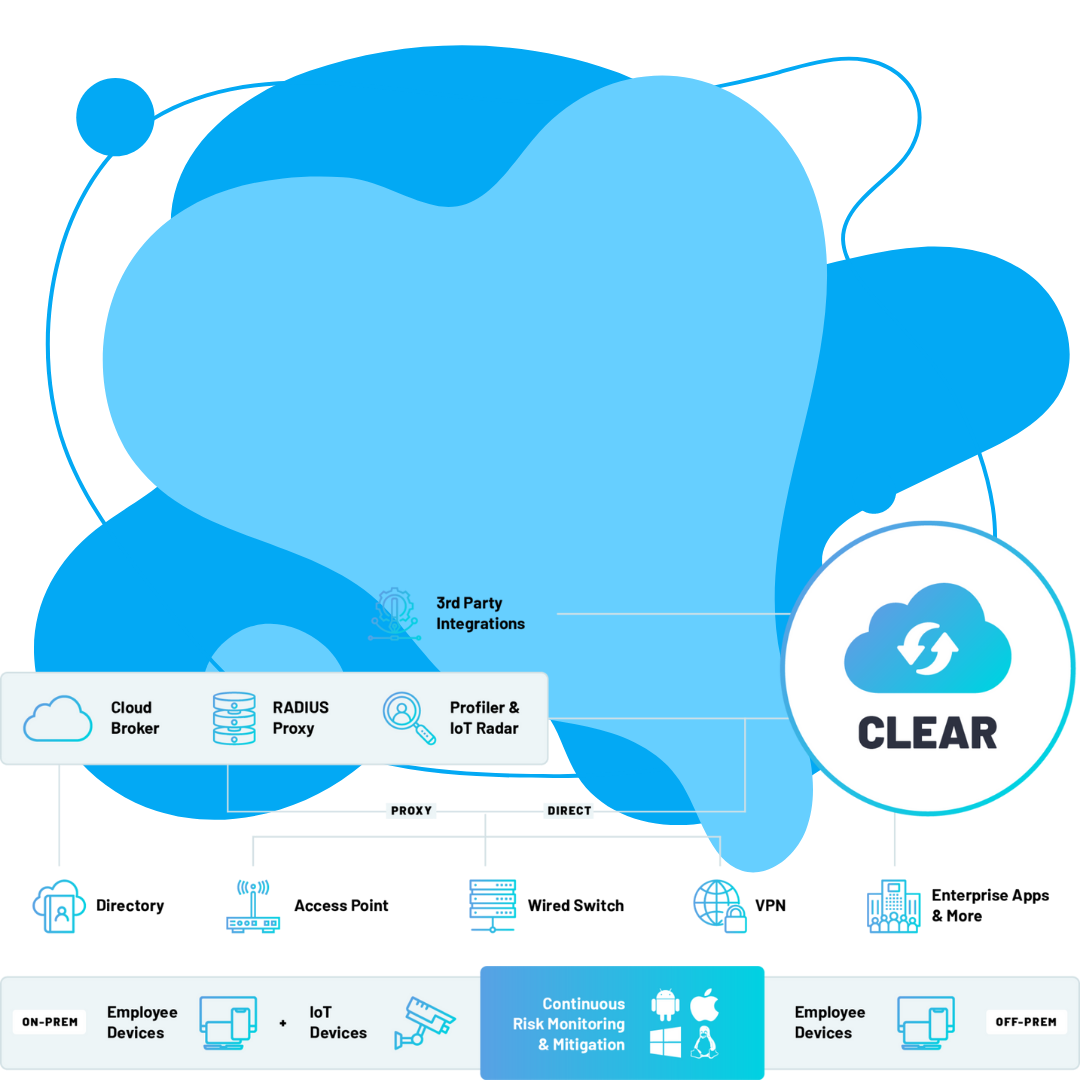
Architecture: Cloud-native, Azure-hosted, No upgrades, No patches, No appliances, Vendor agnostic
Authentication: 802.1X, Directories, Certificates, PKI services, MAC bypass, Account lifecycle synchronization
Access Control: Role-based, Location-based, Segmentation, Guest access, Remote access, Terminal access
Risk Mitigation: Quarantining, Risk scoring, Firewall checks, Antivirus checks, Application checks, USB checks, and more.
Compliance: Firewall stop/start, Antivirus stop/start, Device remediation, Policy enforcement, and more.
Integrations: Azure AD, Okta, Google Workspace, SIEM, EDR, Open LDAP, RESTful API.
Why Portnox NAC?
No matter the size and make-up of your network, our network access control (NAC) solution is easy-to-deploy and manage, and delivers all the security essentials to keep the data on your network.
Powerful
All the functionality you need from an enterprise-grade NAC solution, without any of the complex configuration, expensive customization & ongoing maintenance.
Easy
100% SaaS, true-cloud approach to network access control means you can deploy rapidly without having to worry about on-premise hardware, hidden costs and vendor lock-in.
For Geeks
Portnox CLEAR has been built from the ground up by geeks, for geeks. We know what's important to you because we're just like you - and we're happy to prove it.
Cloud NAC On-Prem NAC
If you can move NAC to the cloud, you should. There is a myriad of benefits to doing so. At a high level, these include operational time savings thanks to easier deployment and less ongoing maintenance, better accessibility (especially for distributed enterprises), more flexibility as your business needs change, etc. In general, enterprises are increasingly adopting purpose-built cloud technologies for different operational needs, and NAC is no exception.
Portnox Core — On-Premise NAC
Today's leading on-premise NAC security solution. Designed with actionable network visibility and control in mind.
Portnox Clear — Cloud-Native NAC
The only cloud-native, a vendor-agnostic platform that unifies network authentication, risk mitigation, and compliance enforcement.
Gain real-time visibility of endpoints trying to connect to your network, plus additional context such as their location, device type, and requested access layer for authentication.
This applies to managed company devices, BYOD and IoT / OT alike, no matter if they're authenticating via wired ports, WiFi, or VPN.
Define and enforce unique access control policies based on roles, locations, device types, and more across your various network access layers.
Additionally, leverage Portnox CLEAR's powerful risk assessment policy configuration capabilities to continually monitor the risk posture of connected devices - including managed and BYOD - enabling your network administrators to understand the true security posture of the network at any point in time.
Quarantine vulnerable, non-compliant devices and return them to a healthy, compliant state automatically by setting unique endpoint remediation policies in accordance with your compliance requirements.
Portnox CLEAR's compliance enforcement capabilities can help your organization adhere to industry-specific regulatory and compliance standards such as HIPAA, GLBA, PCI DSS, GDPR, and beyond.
The security essentials you want. All in one place.
RADIUS
Authentication
Role-based authentication.
MAC authentication bypass.
Certificate authority services.
Visibility
Monitoring-only mode.
Archived device data retention.
Managed, BYOD & IoT profiling.
Control
Role- & location-based access.
Policy group assignment per device type.
Auto-segmentation of users.
Mitigation
Endpoint risk posture assessment.
Risk-based access control.
Firewall, antivirus & app checks.
Reporting
Device visibility & connection timeline.
Guest access history.
Security & compliance adherence.
Form Heading
Sign up, test & deploy in days.
Portnox Network Access Control
Request trial
Get a free 30-day trial of Portnox CLEAR.
Connect Network
Point our cloud RADIUS to your select networking hardware. (3 minutes)
Configure Policies
Configure your unique network access and risk policies. (30 minutes)
Fully Deploy
Complete testing and fully deploy across your entire network. (30 days)
YEARS OF WORK
VENDORS
USE CASES
TrapX DeceptionGrid
DeceptionGrid from TrapX is the only Deception platform that delivers both comprehensive protection and full visibility at scale. In just minutes, patented emulation technology launches hundreds of authentic traps that engage attackers and malware and generate high-fidelity alerts for rapid response.
Cyberbit Range
Cyberbit Range is a hyper-realistic cyber simulation platform that uses flight simulation disciplines to train, onboard, and dramatically improve the performance of incident response teams.
By training in cyber range exercises your team will excel, both technically and mentally when the real attack takes place.
LogRhythm SIEM
LogRhythm Security information and event management is a combination of information security management (SIM) and security event management (SEM) systems into a single security management system.
Available: SIEM technology can reside either on-premise (on your own hardware) or in the cloud (on someone else’s hardware) and collect data from a massive variety of data sources.

