Waterfall schützt Industrien seit 2007:
Eisenbahnen
Öl- und Gasversorger
Kraftwerke
Produktion
Wasserversorger
Chemische Industrie
Merkmale der unidirektionalen Wasserfall-Sicherheitsgateway:
■ Die Hardware ist modular, flexibel und vom Benutzer wartbar.
■ 1 Gbit/s Standarddurchsatz, höhere Durchsatzoptionen verfügbar.
■ Optionale HA-Konfiguration (Hochverfügbarkeit).
■ Anschlüsse an der Vorderseite vereinfachen Sicherheitsaudits.
■ Große Auswahl an COTS-Softwarekonnektoren.
■ Flexibles Connector-Hosting auf Windows, Linux und anderen Betriebssystemen.
Was spricht für Waterfall Unidirectional Security Gateways?
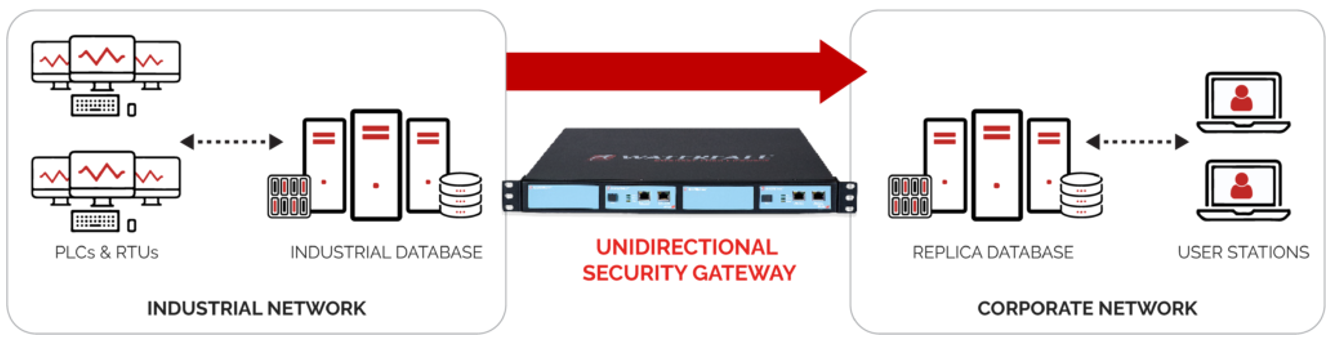
Waterfall Unidirectional Gateways lassen Echtzeitinformationen nur aus einem industriellen Netzwerk heraus fließen. Datenströme in die Gegenrichtung sind ausgeschlossen.
Schlüsselfähigkeiten Waterfall Unidirectional Security Gateways
Weniger Ausfallzeit
Stellen Sie die Betriebskontinuität sicher, indem Sie Anlagenstillstände und Sachschäden sowie Gefahren für die Umwelt und die öffentliche Sicherheit verhindern.
Plug-and-play Lösung
Mehr als 100 Software-Konnektoren verfügbar, kommerzielle Standardlösungen.
Stärker als Firewalls
Eine revolutionäre Alternative zu Firewalls in einem starken vorbeugenden Cybersicherheitsprogramm für industrielle Steuerungssysteme.
Unpassierbare physische Barriere
Unidirektionale Gateways umfassen sowohl Hardware, die absolut vor Cyberangriffen schützt, als auch Software, die unternehmensweite Abdeckung für OT-Transparenz bietet.
Form Heading

INSIDER INSIGHTS: DIE TOP 20 CYBERATTACKEN DER LETZTEN JAHRE (EN)
№1. ICS Insider
A disgruntled control-system technician steals passwords by “shoulder surfing” other technicians, logs in to equipment controlling the physical process using the stolen passwords and issues shutdown instructions to parts of the physical process, thus triggering a partial plant shutdown.
№2. IT Insider
A disgruntled IT insider “shoulder-surfs” remote access credentials entered by an ICS support technician who is visiting a remote office. The disgruntled insider later uses the redentials to log into the same distant ICS engineering workstation that the technician logged into. The insider looks around the workstation and eventually finds and starts a development copy of the plant HMI. The insider brings up screens at random and presses whatever buttons seem likely to cause the most damage or confusion. These actions trigger a partial plant shutdown.
№3. Common Ransomware
An engineer searching for technical information from an ICS-connected engineering workstation accidentally downloads ransomware. The malware exploits known vulnerabilities that have not yet been patched on the industrial network, encrypts the engineering workstation, and spreads to most Windows hosts in the ICS. Most Windows hosts in the industrial network are thus encrypted by the attack, shutting down the control system. The impaired control system is unable to bring about an orderly shutdown. Within a few minutes, the plant operator triggers an emergency safety shutdown.
№4. Targeted Ransomware
An attacker with good computer knowledge targets IT insiders with phishing attacks and malicious attachments, gaining a foothold on the IT network with Remote Access Tool (RAT) malware. The attacker uses the RAT to steal additional credentials, eventually gaining remote access to an industrial control system. The attacker seeds ransomware throughout the ICS and demands a ransom. The site quickly disables all electronic connections between the affected plant and outside networks and tries to pay the ransom. The payment mechanism fails, and the ransomware automatically activates, having received no signal from the attacker that the ransom was paid. The ransomware erases hard drives and BIOS firmware in all infected equipment. The plant suffers an emergency shutdown.
№5. Zero-Day Ransomware
An intelligence agency mistakenly leaves a list of zero-day vulnerabilities in operating systems, applications, and firewall sandboxes on an Internet-based command and control center. An attack group, similar to the “Shadow Brokers” who discovered the US National Security Agency (NSA) zero-days, discovers the list and sells it to an organized crime group. This latter group creates autonomous ransomware that propagates by exploiting the zero-day vulnerabilities in file sharing software in the Windows operating system. The malware is released simultaneously on dozens of compromised websites world-wide, and immediately starts to spread. At industrial sites able to share files directly or indirectly with IT networks, the malware jumps through firewalls via encrypted connections to file shares. The compromised file shares infect and encrypt the industrial site, causing an emergency shutdown and damaging physical equipment.
№6. Ukrainian Attack
A large group of hacktivist-class attackers steal IT remote-access passwords through phishing attacks. These attackers eventually compromise the IT Windows Domain Controller, create new accounts for themselves, and give the new accounts universal administrative privileges, including access to ICS equipment. The attackers log into the ICS equipment and observe the operation of the ICS HMI until they learn what many of the screens and controls do. When the group attacks, the attackers take control of the HMI and use it to mis-operate the physical process. At the same time, co-attackers use their administrative credentials to log into ICS equipment, erase the hard drives, and where practical, erase the equipment firmware.
№7. Sophisticated Ukrainian Attack
A group of attackers is more sophisticated with respect to cyber-attack tools and the engineering details of electric systems. The attack group phishes a low-volume remote access trojan (RAT) into the IT network, such as the BlackEnergy trojan that was reportedly found on IT networks of the utilities impacted by the Ukrainian attack but was not implicated in the attack. With the RAT, the attackers search for and find additional credentials, eventually compromising the enterprise domain controller. The attack group creates credentials for themselves and logs into ICS servers, reseeding their RAT on the ICS network and ultimately taking over equipment on the ICS network. Once inside the ICS network, the attack group connects to protective relays and reconfigures them, effectively disabling the relays. The group now sends control commands to very quickly connect and disconnect power flows to parts of the grid, damaging large rotating equipment such as the pumps used by water distribution systems. The attackers also redirect power flows in the small number of high-voltage transmission substations managed by the distribution utilities, destroying high-voltage transformers by overloading and overheating them.
№8. Market Manipulation
An organized crime syndicate targets known vulnerabilities in Internet-exposed services and gains a foothold on IT networks. They seed RAT tools into the compromised system, eventually gaining Windows Domain Admin privileges. The attackers reach into ICS computers that trust the IT Windows domain and propagate RAT technology to those computers. Because the ICS computers are unable to route traffic to the Internet, the attackers route the traffic via peer-topeer connections using compromised IT equipment. Once in the ICS network, attackers download and analyze control system configuration files. They then reprogram a single PLC, causing it to mis-operate a vital piece of physical equipment, while reporting to the plant HMI that the equipment is operating normally. The equipment wears out prematurely in a season of high demand for the plant's commodity output. The plant shuts down for emergency repair of this apparently random equipment failure. The same attack occurs at two nearby plants. Once the equipment has failed, the perpetrators erase all evidence of their presence from the affected plants' ICS networks. Prices of the commodity produced at the affected plants spike on commodities markets. When plant production at all plants returns to normal, commodity prices return to normal. Before and after the attack, the attackers routinely speculate on futures markets for the affected commodity. That these attackers make large profits when commodity prices spike unexpectedly is seen by any potential investigators as normal and legal. The attack is repeated in the next season of high demand.
№9. Sophisticated Market Manipulation
Sophisticated attackers carry out the market manipulation attack but in a way that is more difficult to defeat. They use known vulnerabilities in Internet-facing systems to compromise the IT network of a services company known to supply services to their real target. The attackers write their own RAT malware and deploy it only at the services company, so that antivirus tools at the services company cannot detect the RAT. The attackers use the RAT to compromise the laptops of personnel who routinely visit the real target. When the attackers detect that the compromised laptops are connected to the real target's IT network, the attackers operate the RAT by remote control and propagate the RAT into the target's IT network. Inside the target's IT network, the attackers continue to operate the RAT. Intrusion detection systems are blind to the activity of the RAT, because the attack is low-volume, using command lines rather than remote-desktop-style communications. The RAT's command-and-control communications are steganographically-encoded in benign-seeming communications with compromised websites. The attack ultimately propagates to the ICS network, with the same consequences as the Market Manipulation attack.
№10. Cell-phone WIFI
Sophisticated attackers seek to inflict damage on a geography they are unhappy with for some reason. The attackers create a useful, attractive, free cell phone app. The attackers use targeted social media attacks to persuade office workers at critical infrastructure sites in the offending geography to download the free app. The app runs continuously in the background of the cell phone. While at their criticalinfrastructure workplaces, the app instructs the phone to periodically scan for Wi-Fi networks and report such networks to a command and control center. The attackers again, use social media, social engineering and phishing attacks to impersonate insiders at their target organizations, and extract passwords for the Wi-Fi networks. Several of these passwordprotected networks are part of critical-infrastructure industrial control systems. The attackers log into these networks using the compromised cell phones and carry out reconnaissance by remote control until they find computer components vulnerable to simple denial of service attacks, such as erasing hard drives or SYN floods. The attackers compromise plant operations, triggering an unplanned shutdown. They then disconnect from the Wi-Fi networks, and then repeat this attack periodically. Variation: Instead of a cell-phone app, attackers use phishing attacks to seed malware on to the desktop computers of office workers who work at the targeted industrial sites, within physical range of ICS Wi-Fi networks.
№11. Hijacked Two-Factor
Sophisticated attackers seek to compromise operations at an industrial site protected by bestpractice industrial security. They write custom RAT malware to evade antivirus systems and target support technicians at the industrial site using social media research and targeted phishing emails. The support technicians activate malware attachments and authorize administrative privileges for the malware because they believe the malware is a video codec or some other legitimate-seeming technology. Rather than activate the RAT at the industrial site, where the site's sophisticated intrusion detection systems might detect its operation, the attackers wait until the technician victim is on their home network but needs to log into the industrial site remotely to deal with some problem. The technician activates their VPN and logs in using two-factor authentication. At this point the malware activates, moving the Remote Desktop window to an invisible extension of the laptop's screen and shows the technician a deceptive error message, such as “Remote Desktop has stopped responding. Click here to try to correct the problem.” The malware provides remote control of the invisible Remote Desktop window to the attackers. The technician starts another Remote Desktop session to the industrial site, thinking nothing of the interruption. In this way, sophisticated attackers have access to industrial operations for as long as the technician's laptop and VPN are enabled. The only hint of the problem that the ICS IDS sees is that the technician logged in twice. The attackers eventually learn enough about the system to mis-operate the physical process and cause serious damage to equipment or cause an environmental disaster through a discharge of toxic materials.
№12. IIoT Pivot
Hacktivists unhappy with the environmental practices of an industrial site learn from the popular press that the site is starting to use new, state-of-the-art, Industrial Internet of Things edge devices from a given vendor. The attackers search the media to find other users of the same components, at smaller and presumably less-well-defended sites. The hacktivists target these smaller sites with phishing email and gain a foothold on the IT and ICS networks of the most poorly-defended of these IIoT client sites. The hacktivists gain access to IIoT equipment at these poorly-defended sites and discover that the equipment is running an older version of Linux with many known vulnerabilities, because the poorly-defended site has not updated the equipment firmware in some time. The attackers take over one of the IIoT devices. After looking at the software installed on the device, they conclude that the device is communicating through the Internet with a database in the cloud from a well-known database vendor. The attackers download Metasploit to the IIoT device and attack the connection to the cloud database with the most recently-released exploits for that database vendor. They discover that the cloud vendor has not yet applied one of the security updates for the database and the attackers take over the database servers in the cloud vendor. In their study of the relational database and the software on the compromised edge devices, the hacktivists learn that the database has the means to order edge devices to execute arbitrary commands. This is a “support feature” that allows the central cloud site to update software, reconfigure the device, and otherwise manage complexity in the rapidly-evolving code base for the cloud vendor's IIoT edge devices. The hacktivists use this facility to send commands, standard attack tools and other software to the Linux operating system in the edge devices in the ICS networks the hacktivists regard as their legitimate, environmentally-irresponsible targets. Inside those networks, the attackers use these tools and remote-command facilities to carry out reconnaissance for a time and eventually erase hard drives or cause what other damage they can, triggering unplanned shutdowns. In short, hacktivists attacked a heavily-defended client of cloud services by pivoting from a poorly-defended client, through a poorly-defended cloud.
№13. Malicious Outsourcing
An industrial site has outsourced a remote support function to a control system component vendor – for example: maintenance of the plant historian. The vendor has located their worldwide remote support center in a country with an adequate supply of adequately-educated personnel and low labour costs. A poorly-paid technician at this support center finds a higherpaying job elsewhere. On the last day of employment, this technician decides to take revenge on personnel at a specific industrial client – the same personnel who recently complained to the technician's manager about the technician's performance. The technician logs into the client site using legitimately-acquired remote access credentials, two-factor credentials and the permanent VPN connection to the targeted site. The technician logs into all the site's control system computers for which the credentials provide access and leaves a small script running on each that, one week later, erases the hard drives on each computer.
№14. Compromised Vendor Website
Most sites trust their ICS vendors – but should those vendors' websites be trusted? Hacktivists find a poorly-defended ICS vendor website and compromise it. They download the latest copies of the vendor software and study it. They learn where in the system the name or some other identifier for the industrial site is stored. These attackers are unhappy with a number of industrial enterprises for imagined environmental or other offences and search the public media to determine which of these enterprises use the compromised vendor's software. The attackers use the compromised website to unpack the latest security update for the ICS software and insert a small script. The attackers repack the security update, sign the modified update with the private key on the web server, and post the hacked update as well as a new MD5 hash for the update. Over time, many sites download and install the compromised update. At each target, the script activates. If the script fails to find the name of the targeted enterprise in the control system 14 16 being updated, the script does nothing. When the script finds the name, it installs another small script to active one week later, erasing the hard drive and triggering an unplanned and possibly uncontrolled shutdown. The one-week delay in consequences makes tracing the attack back to the software update somewhat more difficult.
№15. Compromised Remote Site
In a SCADA system such as might control an electric distribution system or water distribution system, an attacker targets a substation or pumping station that is physically remote from any potential witnesses. The attacker physically cuts the padlock on a wire fence around the remote station and enters the physical site. The attacker locates the control equipment shed – typically the only roofed building at the site – and again forces the door to gain entry to the shed. The attacker finds the only rack in the small site, plugs a laptop into the Ethernet switch in the rack, and tapes the laptop to the bottom of a piece of computer equipment low in the rack where it is unlikely to be detected. The attacker leaves the site. An investigation ensues, but the investigators find only physical damage and nothing apparently missing. The extra laptop low in the rack is not noticed. A month later, the attacker parks a car near the remote site and interacts with the laptop via Wi-Fi, enumerating the network and discovering the connections back into the central SCADA site. The attacker uses the laptop to break into equipment at the remote site, and from there into the central SCADA system. The attacker then uses Ukraine-style techniques to cause physical shutdowns.
№16. Vendor Back Door
An industrial site has outsourced a remote support function to a control system component A software developer at a software vendor inserts a back door into software used on industrial control systems networks. The software may be ICS software or may be driver, management, operating system, networking, or other software used by ICS components. The back door may have been installed with the approval of the software vendor as a “support mechanism” or may have been installed surreptitiously by a software developer with malicious intent. The software checks the vendor website weekly for software updates and notifies the user through a message on the screen when an update is available. The software also, unknown to the end user, creates a persistent connection to the update notification website when the website so instructs, and permits personnel with access to the website to operate the machine on the ICS network remotely. Hacktivist-class attackers discover this back door and compromise the vendor's software-update website with a password-phishing attack. The attackers then use the back door to impair operations at industrial sites associated with businesses the hacktivists have imagined that they have some complaint against. Note that antivirus systems are unlikely to discover this back door, since this is not the autonomously-propagating kind of malware that AV systems are designed to discover. Sandboxing systems are unlikely to discover it either, since the only network-aware behavior observable by those systems is a periodic call to a legitimate vendor's software update site asking for update instructions.
№17. Stuxnet
Sophisticated attackers target a specific and heavily-defended industrial site. They first compromise a somewhat less-well-defended services supplier, exfiltrating details of how the heavily-protected site is designed and protected. The adversaries develop custom, autonomous malware to target the heavily-defended site specifically and bring about physical damage to equipment at the site. The autonomous malware exploits zero-day vulnerabilities. Service providers carry the malware to the site on removable media. Antivirus scanners are blind to the custom, zero-day-exploiting malware.
№18. Hardware Supply Chain
A sophisticated attacker compromises the IT network of an enterprise with a heavily-defended industrial site. The attacker steals information about which vendors supply the industrial site with servers and workstations, as well as which vendors routinely ship such equipment to the site. The attacker then develops a relationship with the delivery drivers in the logistics organization, routinely paying drivers modest sums of money to take two-hour lunch breaks, instead of one-hour breaks. When IT intelligence indicates that a new shipment of computers is on its way to the industrial site, the agency uses the two-hour window to break into the delivery van, open the packages destined to the industrial site, insert wirelessly-accessible single-board computers into the new equipment, and repackage the new equipment so that the tampering is undetectable. Some time after IT records show that the equipment is in production, the attackers access their embedded computers wirelessly, to manipulate the physical process. The attackers eventually impair equipment protection measures, crippling production at the plant through what appear to be a long sequence of very unfortunate random equipment failures.
№19. Nation-State Crypto Compromise
A nation-state grade attacker compromises the PKI encryption system, either by stealing certificates from a well-known certificate authority, or by breaking a popular crypto-system and so forging certificates. The attacker compromises Internet infrastructure to intercept connections from a targeted industrial site to software vendors. The attacker deceives the site into downloading malware with what appears to be a legitimate vendor signature. The malware establishes peer-to-peer communications that are steganographically tunneled through ICS firewalls and DMZs on what appear to be legitimate vendor-sanctioned communications channels. The nation-state adversary operates the malware by remote control, learning about the targeted site. The adversary creates custom attack tools which, when activated, cause the release of toxins into the environment, serious equipment damage and a plant shutdown.
№20. Sophisticated Credentialed ICS Insider
A sophisticated attacker bribes or blackmails an ICS insider at an industrial site. The insider systematically leaks information to the attackers about the design of the site's physical process, control systems and security configurations. The attacker develops custom, autonomous malware designed to defeat the deployed security configurations. The insider deliberately releases the malware on the system with the insider's credentials. A few hours later the malware activates. A day later, there is an explosion that kills several workers, causes a billion dollars in damage to the plant, and shuts the site down for 12-18 months.
EMPFEHLUNGEN FÜR IHRE OT SICHERHEIT
Das oberste Ziel eines OT-Sicherheitsprogramms mit der Absicht, einen Cyber-Vorfall zu überleben, ist der kontinuierliche und zuverlässige Betrieb während des gesamten Vorfalls. IT-Netzwerke sind Ransomware-Angriffen viel stärker ausgesetzt, als es OT-Netzwerke sein sollten, daher ist davon auszugehen, dass IT-Netzwerke viel häufiger verletzt werden als OT-Netzwerke. Daher muss für viele Branchen die Automatisierung so gestaltet werden, dass der Betrieb auch dann sicher und kontinuierlich weiterlaufen kann, wenn das stärker exponierte IT-Netzwerk gefährdet ist.
Secure Operations Technology (SEC-OT) ist die Methode, die von den sichersten Standorten verwendet wird, um dieses Ziel eines sicheren, kontinuierlichen und korrekten Betriebs zu erreichen. SEC-OT-Standorte verwalten Angriffsinformationen so gründlich, dass die Übertragung von Angriffsinformationen in Betriebsnetzwerke, sei es absichtlich oder versehentlich, praktisch unmöglich ist. Mit starken SEC-OT-Schutzmaßnahmen wie Wechselmedienkontrollen, und unidirektionaler Gateway-Technologie können Ransomware-Angriffe die industriellen Kontrollsysteme, die physische Infrastrukturen und Herstellungsprozesse betreiben, nicht erreichen und somit keine Fehlfunktionen dieser Prozesse verursachen.
Besondere Erwähnung verdient die Kontrolle der Abhängigkeiten von Cloud-Diensten. Ransomware, die über Cloud-Dienste bereitgestellt wird, kann nicht nur eine Fabrik oder einen physischen Betrieb lahmlegen, sondern alle Vorgänge, die den kompromittierten Cloud-Dienst verwenden. Das Verhindern einer solchen Kompromittierung ist einfach – sichere Standorte können die Vorteile industrieller Cloud-Dienste sicher nutzen, indem sie sich nur über eine hardwaregestützte unidirektionale Gateway-Technologie mit diesen Diensten verbinden.
Die Hardware schützt, während die Software eine Verbindung herstellt
Zertifizierung & Compliance
Waterfall Unidirectional Security Gateways
Zertifizierungen:
Common Criteria EAL 4+, ANSSI CSPN, NITES Singapore, Korean KC Certification und Israel NISA.
Assessments:
Idaho National Labs, Digital Bond Labs.
Compliance zu:
Global ICS Standards & Regulations, NERC CIP, IEC 62443, NRC 5.71, NIST 800-82r2, CFATS, ISO, IIC SF, ANSSI, uvm.
JAHRE ERFAHRUNG
HERSTELLER IM PORTFOLIO
ANWENDUNGSFÄLLE

Paul Zhdanovych
