Cymulate lets you improve your security posture 24X7X365 within minutes, in just three simple steps:
1. Simulate. Simulate attacks across any vector.
2. Evaluate. Know where your company is exposed.
3. Remediate. Fix your security gaps.
Who Cymulate are?
With a Research Lab that keeps abreast of the very latest threats in the wild, Cymulate proactively challenges security controls, allowing hyper-connected organizations to avert damage and stay safe. Cymulate was founded by an elite team of former IDF intelligence officers and leading cyber researchers with world-class experience in offensive cyber solutions.
Cymulate is trusted by companies worldwide, from small businesses to large enterprises, including leading banks and financial services. They share Cymulate's vision - to make it simple for anyone to protect their company with the highest levels of security. Because the simpler cybersecurity is, the more secure your company - and every company.
Why Cymulate?
Cymulate BAS — Know, Control, and Optimize Your Cybersecurity Posture
Cymulate is an award-winning SaaS-based Breach and Attack Simulation (BAS) platform that makes it simple to know and optimize your security posture any time, all the time.
Fully automated and customizable, Cymulate challenges your security controls against the full attack kill chain with thousands of simulated cyber attacks, both common and novel. Testing both internal and external defenses, the attack simulations show you exactly where you’re exposed and how to fix it-making security fast, continuous, and part of every-day activities.
With 360° visibility and actionable reporting, Cymulate shortens test cycles and offers a counter-breach assessment technology that empowers security leaders to validate the effectiveness of their current security controls by taking a proactive approach to their cyber stance, so they can stay one step ahead of attackers. Always.
The only SaaS-based Continuous Security Validation platform to operationalize the MITRE ATT&CK framework end-to-end
Web Gateway
Validate the effectiveness of your web security controls against threat evolutions and stop attacks in the pre-exploitation stage.
Web Application Firewall
Validate the effectiveness of your Web Application Firewall against threat evolutions and stop attacks in the pre-exploitation stage.
Endpoint Security
Validate the effectiveness of your endpoint security against threat evolutions.
Immediate Threat Intelligence
Expedite security testing of immediate threats and keep up with threat evolutions.
Full Kill Chain APT
Validate the effectiveness of your security architecture, detections and response playbooks to full kill chain APT attacks.
Form Heading
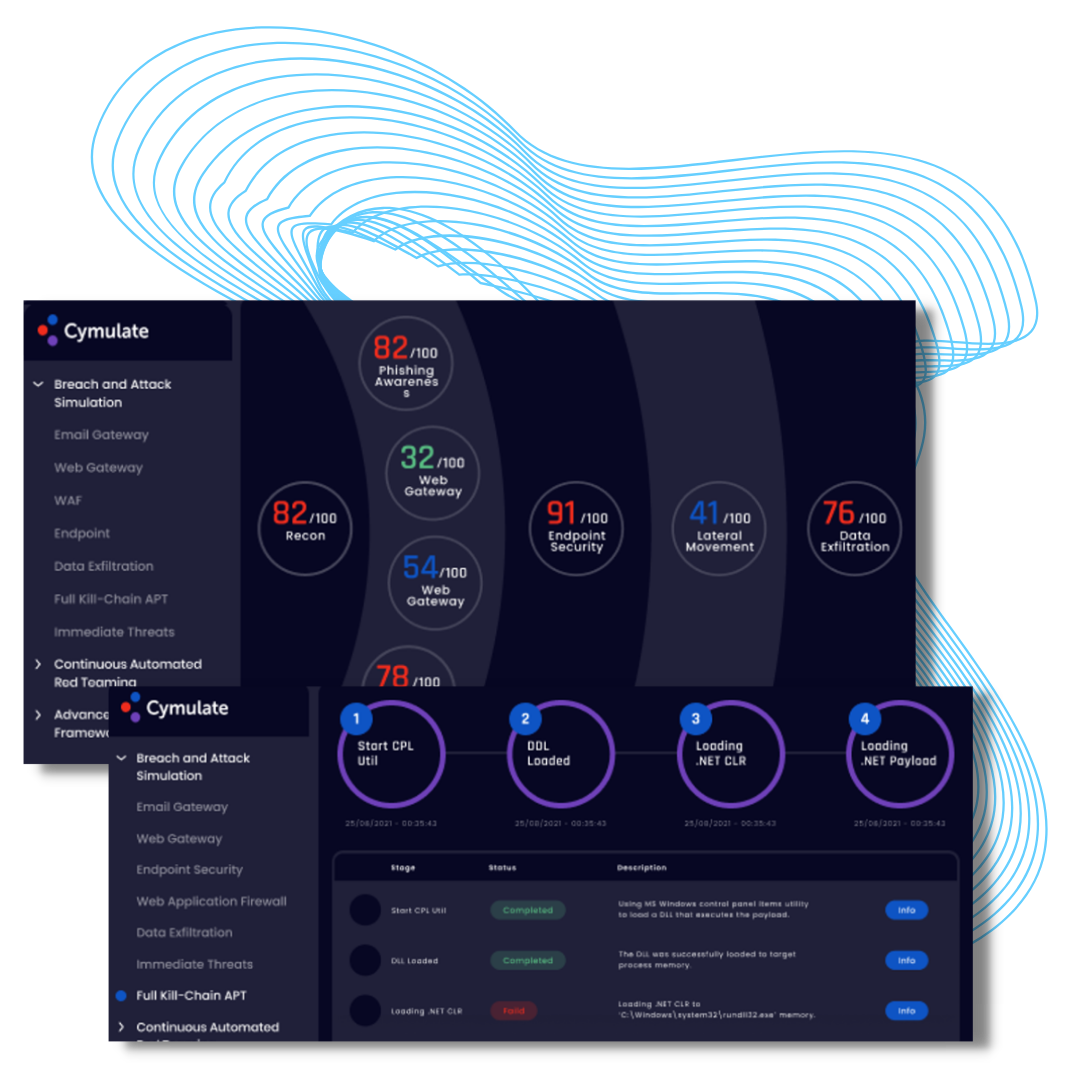
Cymulate BAS Platform:
Email Gateway
Email is the most frequently used method of attack for exploiting security weaknesses and compromising corporate environments. Research shows that over 75% of cyberattacks worldwide originate from a malicious email, and the number of those targeted attacks keep increasing. As we have seen in the past, both very high-profile cyber campaigns as well as less known ones, are launched with an email containing a malicious attachment or link for infecting victims with ransomware or opening a direct connection to the Command & Control (C&C) servers of hackers.
For example, a recurring DHL themed phishing template used during the holiday season spreads different malicious payloads such as Tesla, Panda, Ursnif etc. One recent example of this method used a DHL themed shipment invoice sent by email, notifying its victims that there is a new shipment waiting for them. Victims that click on the link or open attachments download a dropper that links to the attacker’s C&C server downloading malware to the victim’s endpoint, thus compromising it, and in some cases even compromising the whole organization.
Organizations utilize different security controls, such as Secure Email Gateways (SEGs), Sandbox, and Content Disarm and Reconstruction (CDR) solutions to protect their employees’ mailboxes. However, their incorrect configuration or implementation can lead to the false assumption that an organization is safe.
Cymulate’s Email Gateway vector evaluates your organization’s email security and potential exposure to malicious payloads and links sent by email.
Web Gateway
Unsecure web browsing is frequently abused by hackers to exploit security weaknesses and compromise corporate environments. The World Wide Web is filled with malicious websites, and new ones are created every day.
Furthermore, legitimate websites developed in an insecure manner are also being compromised and used to spread malware and other attacks.
Cymulate’s Web Gateway vector simulates a myriad of web-based attacks that challenge and assess the efficacy of your web security controls. These controls include cloud and on prem secure web gateways and proxies, content disarm and reconstruction technologies, sandboxing and other types of web-security controls. The Web Gateway vector enables you to measure your organization’s exposure to an extensive and continuously updated database of malicious and compromised websites, malware, and risky files used by threat actors in web-based attacks.
Technical reports provide analysis of the attacks and actionable mitigation guidance that help security teams to shore up their defenses against successful attacks. Standards-based risk scoring enables IT and security teams to identify security gaps, prioritize mitigations and take corrective measures to increase web security control efficacy. Executive reports include trend analysis to identify security drift and industry-peer benchmarking to gain comparative insights.
Web Application Firewall
Web Applications are a core component in business operations. As these process sensitive data, huge amounts of money and effort are spent protecting these assets. In the past IT security teams just had a few enterprise web apps to defend. Now they need to protect the web back-end of multiple and varied mobile apps, SaaS apps and other cloud-delivered solutions.
Furthermore, the number and diversity of threats continues to increase, from advanced malware to web-specific application-layer attacks, as well as denial and distributed denial of service (DoS, DDoS) attacks and security-induced usability issues. Regarding security, organizations rely on WAF for protecting their web apps. These days, cybercriminals and novice black hats easily find all sorts of automated attack tools and exploit kits online. With such tools, all they need to do is insert a URL address as the target and launch their attack. A successful attack can bring down a website that is used to generate revenue for the organization. Every minute of downtime costs the organization a lot of money, impacts its brand credibility and translates into business loss. A notorious example is the infamous Equifax breach that was caused by an application server vulnerability (Apache Struts) affecting over 140 million consumers.
The Web Application Firewall vector will validate the configuration, implementation, and efficacy, to ensure that the Web Application Firewall blocks malicious payloads before they get to your Web Application. The platform simulates an attacker who tries to bypass your organization’s WAF and reaches the web application, after which they attempt to perform malicious actions, such as mining sensitive information. The assessments use real payloads with benign outcomes that do not put the organization’s web applications at risk.
Technical reports provide analysis of the attacks and actionable mitigation guidance that help security teams to shore up their defenses against web application attacks. Standards-based risk scoring enables IT and security teams to identify security gaps, prioritize mitigations and take corrective measures to increase WAF efficacy. Executive reports include trend analysis to identify security drift and industry-peer benchmarking to gain comparative insights.
Endpoint Security
Unsecure web browsing is frequently abused by hackers to exploit security weaknesses and compromise corporate environments. The World Wide Web is filled with malicious websites, and new ones are created every day.
The Endpoint Security vector challenges your endpoint security controls and checks whether they are properly tuned to defend against signature and behavior-based attacks. Endpoint security is critical to an organizations capability to prevent and detect malicious behaviors and threats. Organizations protect their endpoints with layers of defense such as antivirus, anti-spyware and behavioral detection solutions. They even deploy highly sophisticated deception systems to lead attackers away from the real endpoints and lure them to honeypots and traps.
Cymulate’s Endpoint Security vector allows organizations to deploy and run simulations of full attack scenario’s e.g. ransomware or implementation of MITRE ATT&CK TTPs on a dedicated endpoint in a controlled and safe manner, comprehensive testing that covers all aspects of endpoint security.
Data Exfiltration
Challenge your Data Loss Prevention (DLP) controls to assess their effectiveness in preventing exposure of sensitive information and theft of critical data. Organizations are forced to comply with an increasing number of laws and regulations that set guidelines for the collection, processing and safeguarding of personal and sensitive data, financial information and medical records against theft and misuse. In addition to compliance requirements, data breaches can also result in huge financial impact, and brand and reputation impairment. Stolen intellectual property can destroy a company’s competitive advantage.
DLP solutions are designed to protect against data exfiltration. Organizations depend on DLP implementations, methodology and configuration as their last line of defense to protect their critical data.
The Data Exfiltration vector evaluates how well your DLP solutions and controls prevent any extraction of critical information by employing multiple methods of extraction used by threat actors and by employees who may not be aware that they are violating compliance and internal security policies.
Immediate Threat Intelligence
Every day, new payloads and attacks show up in the wild, orchestrated by known and unknown hostile entities, and while security leaders would like a clear and validated answer to every threat, their security team is unable to research and operationalize threat intelligence fast enough and/or are unable to test security control efficacy at a high enough pace.
Cymulate Immediate Threat Intelligence module replaces these manual processes by providing a prepackaged fully automated assessment of new threats, that are updated daily in the platform by Cymulate Labs researchers. Assessments includes the following:
- Pre-exploitation attacks of the threat used to test email and web security controls.
- Endpoint security threat samples detection/removal.
- Indicators of compromise.
- Vulnerabilities exploited by the threat and vulnerable assets, through integrations with VA/VS systems.
- Detection and mitigation guidance.
Full Kill Chain APT
Are you Advanced Persistent Threat (APT) Ready?
Cymulate makes it simple to validate your security framework and for you to continuously challenge, assess, and optimize the effectiveness of your IT controls in defending against real-world cyberattacks.
Testing Controls Across the Full Kill Chain:
Advanced Persistent Threat (APT) attacks attempt to bypass security controls across the cyber kill chain, from attack delivery to exploitation and post-exploitation, defending against an APT requires testing the effectiveness of multiple security controls within your arsenal. Since the efficacy of one control affects the exposure of the next control in the kill chain, ascertaining if your defenses work against a full-blown attack becomes a daunting proposition.
Cymulate’s Full Kill Chain APT Simulation Module solves the challenge of security effectiveness testing across the entire cyber kill chain. Instead of challenging each attack vector separately, organizations can now run a simulation of a full-scale APT attack with a click of a button, and gain a convenient, single-pane view of security gaps across their security stack.
Product Benefits
Cymulate - simple Breach and Attack Simulation
Customized Attacks
Deploys Seamlessly
Comprehensive Coverage
Immediate Results
YEARS OF WORK
VENDORS
USE CASES
Why cooperation with Softprom?
-
We implement projects together with Cymulate specialists.
-
We select the best packages for your tasks.
-
Support in testing.
-
We provide the possibility of payment in national currency.

